Regulators across the globe are cracking down on ensuring that businesses have robust cyber assessment policies in place. Here’s what businesses need to consider
Businessses face growing pressure from regulators to ensure that cyber risk assessments are fit for purpose.
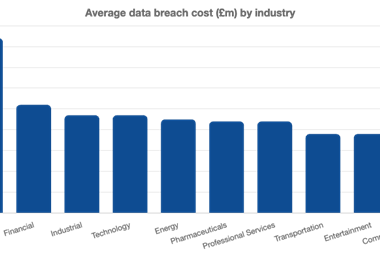
This month, the UK government published its UK Cyber Security Breaches Survey 2025, which found that just over four in ten businesses (43%) experienced a cyber security breach or attack in the last 12 months.

The figure equates to approximately 612,000 UK businesses. It represents a decrease compared to 2024 where 50% experienced a breach or attack, but the number is still alarming.
The study found that phishing remain the most prevalent type of cybercrime, experienced by 85% of those businesses who had experienced a breach or attack.
Meanwhile, in the United States members of the U.S. House Committee on Homeland Security have reintroduced legislation this month to combat growing cyber threats from the Chinese Communist Party (CCP) against the nation’s critical infrastructure sector.
The bill would require the federal government to assess and mitigate growing cyber threats originating in China with either the active or tacit support of the CCP.
The legislation aims to enhance the security and integrity of U.S. critical infrastructure by establishing an inter-agency task force and and a comprehensive report.
Why cyber risk assessments are key
Speaking in an online seminar, Jason Gobbel chief solutions officer at Kite Technology and Ryan Smith, president of specialist cyber security company RLS Consulting both said there was growing pressure on business to ensure their cyber risk assessments were detailed and clearly evidenced.
“Cyber risk assessments are part of you compliance process,” Gobbel explained. “Clients expect you to be good stewards of their data. As a business you need to appreciate that you cannot be secure if you do not know what you are missing.”
Smith added: “Your cyber risk assessment should be focused on understanding the likelihood and the impacts of the risks you face. It helps you to understand how an attack might happen. Ask yourself, what could go wrong, what sensitive data do we have, and what happens if the technology you rely on to operate fails.
“When you understand the risks, you need to score them. You need to go system by system and understand what technology you have and how are you protecting it. How dependent are you in the technology and what if it fails for a period of days or weeks?”
Gobbel said that while much can be achieved internally, third-party vendors including IT suppliers needed to be engaged and you need to come to an agreement on their role in the assessment process.
“To put in in simple terms, your assessment should ask ‘are we immune to being punched in the nose’, he explained. “Where could the punch come from, how much will it hurt and can we doing anything to avoid getting punched. Once you know that you can look at whether there is anything you can do about it other than cry.”
How to carry out a robust cyber risk asssement
One key change with legislation emerging across the globe is that legislators no longer believe that simply carrying out an assessment is enough. Instead, they expert that these processes are robust and comprehensive.
Smith said: “[A cyber risk assessments] will help you understand the overarching plan to get you to where you want to go. It will create accountability and consistency. It will reduce the potential for financial and reputational loss.
“It will enhance customer trust and meet regulatory requirements. It will also guide strategic decisions around cyber security investments. You know what could or will happen and when it does you can leap on things faster.”
Gobbel added: “Analysis paralysis is real. The risk assessment creates the roadmap and the priorities will write themselves.”
He said the core areas for a detailed and robust cyber risk assessment include:
- Identifying assets (laptops, hardware, data, or mobile phone which can access that data)
- Threat identification
- Vulnerability analysis
- Risk evaluation – likelihood and impact.
- Development of mitigation strategies
- Documentation and continuous monitoring
- The production of an executive summary.
“This is very much a case of rinse and repeat,” he added. “At worse once a year you will need to crack the assessment back open. The executive summary needs to go up and down the business. Everyone has a role to play.”
Smith added: “Consistency is the key when it comes to the scoring of your risks as is the ability to communicate what you have found and what needs to be done.”
Getting leadership on board
It is vital that business leaders are part of the process, with regulators now expecting those in the boardroom are well aware of the work undertaken and the actions which had arisen from the result of any assessments.
Smith commented that the risk management team had to ensure the right stakeholders engaged in the applicable stages of the assessment process over and above handing the responsibility to IT department.
He said: “Regulators will want to know how the process was delegated, but the final responsibility will reside with the leadership team.”












No comments yet