What does cyber agility look like for financial institutions navigating rapid change? – 30 senior cyber risk leaders share their eight priorities. By Steve Bishop, research and information director at ORX
How can we stay agile in the face of rapid technological change, geopolitical shifts, customer expectations, and economic factors? This is a question that senior cyber risk leaders ask themselves every day.
We interviewed 30 senior leaders, from CISOs to Heads of Cyber Risk, as part of a Faster & Safer: Priorities for Cyber Risk Management whitepaper and asked them to share their priorities for the next 12-18 months. There was absolute unanimity on one point: the industry must work together.

1. Scale-up (new) technology
Technology and human behaviours are evolving fast, and the need to protect data and other assets is a daily challenge. Combining the complexity of legacy systems adds further burden.
All risk leaders agreed that demands are intensifying but there is also opportunity. Machine learning, APIs and automated processes can be used to analyse risk and control information, monitor control performance and drive control automation.
They also support the use of an open-source model of sharing best practice, models and tooling innovation where in-house solutions can be exploited and evolved across the industry.
2. Know your blind spots
Three-quarters of participants said they need to better understand their full cyber risk exposure and security position scross their end-to-end services and processes.
This means full visibility of both upstream and downstream vulnerabilities and the risks associated with suppliers.
Leaders recognise they must identify blind spots and manage their impact on risk exposures. All agreed that the biggest challenge to this is the complexity of today’s interconnected risk landscape and articulating risk exposure in a language that business understands.
It requires an understanding of the full control environment across the digital supply chain and the complex regulatory landscape. Whatever the approach, the ability to have an informed conversation based on a consistent view of cyber risk exposure is a key industry priority.
3. A move to metrics
Every participant said that they need data-centric, action-orientated decision-making based on industry-standard metrics. In other words, a common set of metrics to identify, assess, and monitor risks and controls.
With this, they can look at peer benchmarking and a consistent approach to reporting cyber risk to business leaders. All agreed that there is work to do to overcome barriers for regular industry sharing of experience.
4. Stay close to third parties
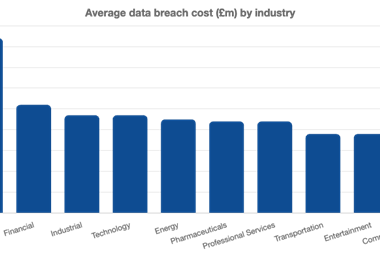
The third-party supply chain can be the weak link in a firm’s cyber resilience with recent data breach examples such as Solarwinds and MOVEit.
All interviewees agreed that oversight of third parties is complex and demand will increase with the added effect of cloud computing bringing additional risk exposure, such as data security & management, third party and concentration risk.
All acknowledge greater collaboration is needed with third parties with clear lines of communication and a good understanding of their risk and control environment. Interviewees cited the upcoming DORA regulation in Europe affects many participants, which will drive a more detailed understanding of this supply chain.
5. Doing risk measurement differently
Cyber risk leaders see the need for robust approaches to risk measurement – traditional operational risk measurement methods and tooling are just not precise enough or suitable for cyber.
They want to deliver data-driven assessments that can inform business decisions, but there is consensus that no one has yet found the optimum approach, particularly due to the volatile and scalable nature of cyber risk.
Most participants are working to identify not just data sources across the organisation but the most effective set of internal and external metrics that can be used for risk measurement. Historical data is often not available, which makes it hard to articulate the full impact of cyber risk.
6. No more manual cyber controls
Firms believe that it is vital that control automation programmes evolve at pace as part of business and technology transformation programmes, and that controls are fully embedded by design.
This will be an iterative process over the coming months and years, but there are workstreams to build new cyber control libraries, identify key controls, and use technology to automate controls, their assessment and monitoring.
The investments in this area are delivering a return, as automation means fewer people are required to operate and assess controls.
7. A ‘when, not if’ mindset for cyber resilience
Cyber is a key consideration in any organisation’s resilience but embedding it requires a shift in thinking to an end-to-end, “resilient aware” mindset. All agree there is a need to shift the organisation to thinking in terms of ‘when, not if’ - a significant challenge given today’s customer expectations of a 24/7 always-available service.
There is a growing need to be able to demonstrate effective controls to recover effectively from a cyber event before the point of customer harm is reached.
This means driving a culture of being resilient and focused on the impact to customers, not just the impact on the organisation, ultimately leading to greater accountability and business awareness.
8. Make better friends with the regulators
As cyber risks increasingly permeate all services, leaders expressed a wish to develop deeper relationships with regulators.
They felt that continuing to build on existing relationships, sharing and establishing a common understanding and language of the cyber risk landscape and threats was a sensible path to reach a mutual goal of protecting the financial services industry.













No comments yet